Most companies now collect and share data and information online because of the considerable advancements made in networking over the years. In turn, they have had to up their game when it comes to data safety during transmission, and this is where Proxy Server come in.
So what are proxy servers, and what is their role in cyber security? Let’s find out.
What is a Proxy Server?
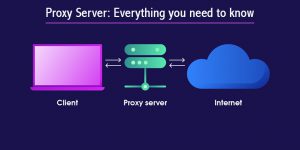
When using the internet to obtain data, individual users and organizations are constantly exposed to numerous cyber threats. Proxy servers offer the additional protection that is required in this situation, thus it is simply a gateway that serves as a data intermediary between a user and the internet.
A proxy server can be a computer system or router that retrieves data from an internet source on behalf of the user. This provides more sophisticated protection and privacy and eliminates the hazards associated with accessing information straight through a browser, such as harmful internet activities.
Types of Proxy Servers
There are many types of proxy servers, and you can pick the most suitable one depending on its application, service, anonymity level, traffic flow, and accessibility. These classifications include
1. Forward Proxy Servers
A forward proxy server passes a user’s request to the internet on an internal network through a firewall. This means that the proxy is configured to either deny or allow your request, depending on the data or website you’re looking to access.
If the proxy approves the request, the forward proxy checks if the requested information is cached. If it is, it delivers it immediately to you, but if not, it transfers it to the web server. On the other hand, it returns an error or redirect message if it rejects your request.
2. Transparent Proxy Servers
Transparent proxies are set by the website or network operator, which explains why they don’t conceal your identifying information. Instead, the request they send to the Web server shows who sent it.
Due to this low level of privacy, transparent proxy servers are the easiest to set up and are used by public libraries, organizations, and schools to filter website content.
3. Anonymous Proxy Servers
Most. users find that anonymous proxy servers frequently offer the highest level of security since they ensure complete privacy. Once you make the request, they conceal your IP address and do not identify themselves to web servers as proxies.
There are two types of anonymous proxy servers. High-anonymity proxy servers routinely change their IP addresses when making web requests, making it hard for users to be identified, while Level 2 anonymous proxies conceal your real IP address by changing geolocations and avoiding targeted marketing.
4. HTTP Proxies
HTTP proxy servers are not configured by a user. Instead, they are configured by the website or browser to save the cache data for every piece of information you access. This improves store access time in case you revisit the site looking for the same information.
Users should exercise caution when accessing HTTP proxies, as they may completely filter out HTTPS connections or only allow you to connect to parts of a website that are unsecured.
What is the Work of Proxy Servers in Cyber Security?
Every internet-connected device has an internet protocol (IP) address, which the internet uses to identify your device and track its online activities.
So, typically, when you access a website by sending a direct request to its web server, it sends a response containing the data that you need, but your address is exposed.
Proxy servers change this by acting as an intermediary between you and web servers for your cyber security needs, and here’s a simple configuration of how they work.
- When you make a request to the internet, the proxy server reads and interprets the contents.
- The server then forwards the request to the relevant web server that you’re seeking information from.
- The internet server only reads the proxy server’s IP address, collects the data, and returns it to the proxy’s IP.
- The proxy server doesn’t send the data directly to your IP address. It reads the data, extracts it, and scans it for malware as it goes.
- The data is subsequently transmitted to your IP after being determined to be secure.
- Proxy servers reduce the possibility of any cyberattacks and offer security from other internet threats by changing the original IP address.
Also Read: Difference Between Web server and Application server
Benefits of Proxy Servers in Cyber Security
The practice of protecting data, network systems, and devices from hostile attacks is known as cybersecurity. Proxy servers, while having a standard procedure, are crucial to cyber security as they safeguard your devices and data when you browse the internet.
While most proxy servers have multiple roles, a few of them have specific capabilities that you should be aware of before employing them. Nevertheless, here are the most common benefits of proxy servers in cyber security
1. Anonymous Browsing
Proxies sit between the internet’s servers and users. This means that your IP address is not exposed to the internet. For individuals, this protects their privacy, and for organizations, their research and development processes are shielded from external threats.
2. Improved Security
Data breaches can be costly, especially for organizations. Up until 2021, the global losses due to cybercrime reached over $6 trillion, which is why a lot of companies turn to proxy servers to hide their IP addresses from internet servers, where they are exposed to threats.
Moreover, proxy servers filter out malicious data from the internet before it reaches your device. While it might not protect you from every cybercrime attempt, this additional layer of security considerably reduces the risk.
3. Faster Speeds
Proxy servers often cache the information that you want from the internet. This means that the proxy won’t have to forward your request to the web server the next time you send repeat queries seeking the same information.
We cannot overlook the importance of proxy servers in cyber security. From providing additional security to making users’ IP addresses anonymous to internet servers, there is every reason to be looking in their direction if you want to access data from the internet.