
Imagine losing $4 billion in market value overnight. That’s exactly what happened to Equifax after their notorious data breach, which also resulted in a $425 million FTC fine.
In times when cybercriminals rake in a staggering $1.5 trillion annually from data theft and ransomware attacks, protecting customer data is a matter of survival.
From insurance industry software that handles sensitive policyholder information to financial services platforms managing transaction data, organizations face unprecedented challenges in safeguarding customer information.
With the average data breach now costing companies $4.88 million, the question isn’t whether you should protect your customers’ data but how well you’re doing it.
Why Customer Data Protection Matters
The consequences of poor data protection extend far beyond immediate financial losses. When a data breach occurs, it triggers a devastating domino effect that can cripple even the most established organizations.
High-profile cases like the Twitter hack of 2020, where attackers seized 130 high-profile accounts and stole over $118,000 in bitcoin within hours, demonstrate how quickly security failures can escalate.
| Consequence | Description |
|---|---|
| Financial Loss | Direct costs from breaches, regulatory fines, and legal penalties |
| Reputational Damage | Loss of customer trust and brand value |
| Business Interruption | Operational disruptions and service outages |
| Legal Issues | Regulatory violations and potential lawsuits |
| Customer Impact | Identity theft, fraud, and privacy violations |
Essential Data Protection Strategies for Protecting Customer Data
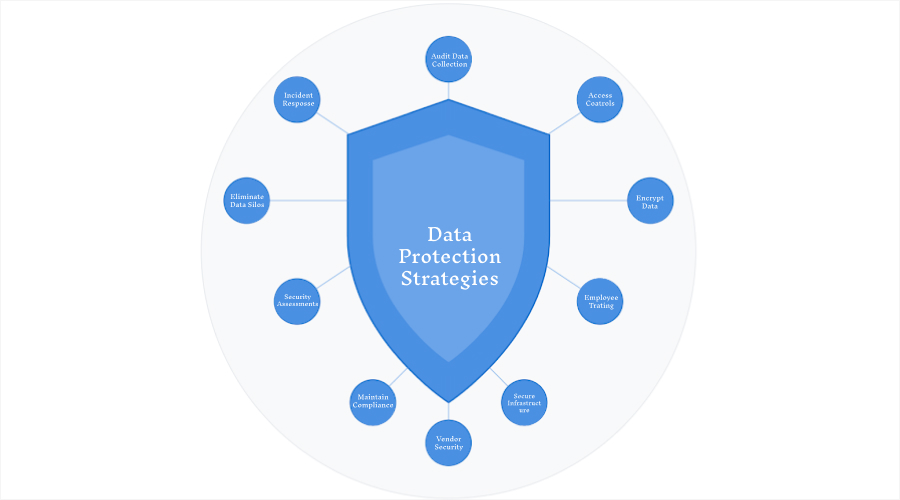
Drawing from industry best practices and lessons learned from major security incidents, we’ve compiled the most effective strategies to protect your customers’ sensitive information.
Each of these approaches works in combination with the others to create a comprehensive security system for your organization.
1. Audit Your Data Collection
Regular data auditing is fundamental to effective security. Most consumers won’t purchase from a company if they doubt its ability to protect their data.
Start by conducting a comprehensive inventory of all data collection points, including:
- Customer touchpoints: Review all places where customer data enters your system, from web forms to mobile apps and in-store collections.
- Data necessity assessment: Evaluate each data point against business objectives to determine if collection is truly necessary.
- Storage location mapping: Document where different types of data are stored across your infrastructure.
- Retention period review: Establish and enforce clear timelines for how long different types of data should be kept.
2. Implement Strong Access Controls
Access control requires a multi-layered approach that ensures data is only accessible to those who truly need it. Implementation should follow a strategic framework:
- Principle of Least Privilege (PoLP): Grant your users the minimum permissions necessary to perform their job functions. This reduces the risk of both accidental and intentional data misuse.
- Identity and Access Management (IAM): Deploy robust IAM tools to centrally manage user identities and access rights across all systems.
- Access monitoring and logging: Maintain detailed records of who accesses what data, enabling quick detection of unusual patterns or potential breaches.
- Regular permission reviews: Conduct quarterly audits of access rights, especially after role changes or departures.
3. Encrypt Sensitive Information
Encryption is your last line of defense against data breaches. Modern security standards demand 256-bit encryption as the minimum for protecting sensitive information.
Your encryption strategy should encompass all data states, from storage to transmission. This includes securing email communications, implementing proper SSL certificates for web traffic, and ensuring file-level security for all sensitive documents.
Don’t forget about key management — even the strongest encryption is only as secure as its key storage system. Implement robust key management procedures and regularly rotate encryption keys to maintain security integrity.
4. Train Your Employees
Security awareness training should be an ongoing process, not a one-time event. Your program must cover:
- Phishing prevention:
- Recognition of suspicious emails and links
- Proper verification procedures for unusual requests
- Reporting protocols for suspected phishing attempts
- Password security:
- Creation of strong, unique passwords
- Proper use of password managers
- Multi-factor authentication procedures
- Data handling:
- Classification of sensitive information
- Proper storage and transmission procedures
- Incident reporting protocols
5. Secure Your Infrastructure
Infrastructure security forms the backbone of your data protection strategy.
Building a secure infrastructure isn’t just about installing antivirus software — it requires a combination of tools, protocols and monitoring systems working in harmony.
The rise of remote work and cloud computing has made this even more critical as traditional network boundaries continue to dissolve.
| Component | Purpose |
|---|---|
| Antivirus Software | Protect against malware |
| Firewalls | Control network traffic |
| MFA | Add authentication layers |
| EDR Tools | Monitor endpoint security |
| Password Managers | Ensure strong credentials |
6. Evaluate Third-Party Vendors
Vendor security has become a critical focus in data protection strategy, as third-party breaches account for a significant portion of data incidents.
When evaluating vendors, start with a thorough security assessment process that examines their compliance standards and security protocols.
Certification requirements should be non-negotiable. Ensure all vendors maintain current SOC 2 compliance and ISO 27001 certification, which demonstrate their commitment to security best practices and continuous monitoring. Regular security audits should be conducted at least annually, with clear documentation of findings and remediation plans.
Data handling policies must be explicitly defined in service level agreements (SLAs). These should cover data storage locations, encryption standards, access controls, and breach notification procedures.
Remember to include right-to-audit clauses in vendor contracts, giving you the ability to verify their security practices firsthand.
7. Maintain Compliance
Stay current with relevant regulations:
- GDPR for European customers
- CCPA for California residents
- HIPAA for healthcare data
- PCI DSS for payment information
8. Regular Security Assessments
Systematic security testing is crucial for maintaining strong defenses. Start with quarterly vulnerability scans across all systems, using both automated tools and manual verification. These scans should identify potential weaknesses before they can be exploited.
Penetration testing should be conducted at least annually by qualified security professionals. These tests simulate real-world attack scenarios, helping identify complex vulnerabilities that automated scans might miss.
Security audits must examine both technical controls and organizational processes. Include reviews of access logs, security configurations and policy implementation effectiveness. Document all findings and track remediation progress.
9. Break Down Data Silos
Data fragmentation poses significant security risks. It’s a good idea to centralize data management so that your organization can better control access, monitor usage and implement consistent security controls.
Create a unified data architecture that eliminates redundant storage and provides clear visibility into data locations and movements. This centralization enables better security monitoring and reduces the attack surface available to potential threats.
Implement data governance frameworks that ensure consistent security controls across all data repositories. Don’t forget about standardized access controls, encryption requirements and audit logging procedures.
10. Incident Response Planning
Develop and maintain:
- Clear response procedures
- Communication protocols
- Recovery strategies
- Documentation requirements
Best Practices for Different Types of Customer Data

Different categories of data require distinct protection approaches. The sensitivity and regulatory requirements vary significantly between personal identification information and basic behavioral data.
Understanding these nuances is crucial — a one-size-fits-all approach to data protection often leaves critical vulnerabilities exposed.
| Data Type | Protection Requirements |
|---|---|
| Personal Identifiable Information (PII) | Encryption, access controls, audit logging |
| Financial Data | PCI DSS compliance, encryption, segregation |
| Health Information | HIPAA compliance, special handling |
| Behavioral Data | Anonymization, consent management |
Also Read: Different Types of Ransomware Attacks
Conclusion
Protecting customer data requires a comprehensive, multi-layered approach. By implementing these strategies and maintaining vigilance, organizations can significantly reduce their risk of data breaches and maintain customer trust.
The cost of prevention is always lower than the cost of a breach. With cybercrime generating approximately $1.5 trillion in annual revenue, organizations must remain proactive in their data protection efforts.
FAQs
Q1. What’s the difference between data privacy and data security?
Data privacy focuses on the appropriate collection, sharing, and usage of data. This includes determining what data should be collected, obtaining proper consent, and ensuring data is only used for its stated purposes.
Data security encompasses the technical implementations and measures that protect data from unauthorized access and cyber threats. This includes technologies like encryption, firewalls, and access controls.
While privacy establishes the rules and principles, security provides the practical tools and methods to enforce those rules. Both aspects must work in harmony to create a comprehensive data protection program.
Q2. How often should we update our data protection policies?
A comprehensive review of data protection policies should occur at least once a year.
Major organizational changes (e.g., entering new markets or launching new services) should trigger immediate policy reviews. Similarly, any security incident, from a minor data exposure to a full-scale breach, necessitates a thorough policy examination.
New regulations or updates to existing ones also demand prompt policy updates. For instance, when the GDPR introduced new requirements for data processing agreements, organizations worldwide had to revise their policies to maintain compliance.
Q3. What should we do after discovering a data breach?
The first priority is containment — identifying and isolating affected systems while preserving evidence for investigation.
A thorough assessment must then determine the scope of compromised data and identify affected individuals.
The incident response team should simultaneously implement immediate security fixes and begin a detailed forensic investigation. This phase requires meticulous documentation, as findings may be crucial for legal proceedings or insurance claims.






