The process of implementing application security (AppSec), known as DevSecOps, is in the mainstream today. It entails incorporating security measures at the beginning of the software development life cycle (SDLC). DevSecOps methodology aims to change not just the mindset of the key functional teams in SDLC but also their procedures and technologies in order to make security a shared responsibility. So, if you want to learn more about DevSecOps, how it impacts software development and DevSecOps Tools, then this post is for you.
Everyone involved in the software development life cycle does their part to ensure security in the CI/CD pipeline.
In this post, we shall walk you through the top DevSecOps Tools to help you select the best DevSecOps Tools.
Let’s plunge in…
Table of Contents
- What is “DevSecOps”?
- How does DevSecOps work?
- How is DevSecOps different from DevOps?
- What are the advantages of utilizing DevSecOps tools?
- Top 10 DevSecOps Tools
- Conclusion
What is “DevSecOps”?
DevSecOps stands for development, security, and operations. In order for DevOps teams to be able to provide secure applications in a timely manner without sacrificing speed or quality, DevSecOps grew out of the necessity to integrate security measures continually throughout the software development life cycle (SDLC).
Using the best DevSecOps tools, developers can eliminate the time-consuming and frequently expensive ramifications of implementing fix postproduction by incorporating testing, triage, and risk mitigation early in the CI/CD workflow.
This gives developers the ability to address security flaws in their code in close to real-time, as opposed to “bolt-on security” towards the end of the software development life cycle (SDLC).
The DevSecOps methodology encompasses the entirety of the SDLC, beginning with the planning and design stages and continuing through the coding, building, testing, and release phases with continuous real-time feedback loops and insights.
The development of software using the DevOps methodology is based on a three-pronged strategy that prioritizes corporate culture, process, and the use of technology and tools. Traditional software development techniques are outpaced by these three alternatives, which are designed to assist development and IT operations teams work together to produce, test, and release software in a manner that is both more agile and more iterative.
In a nutshell, DevSecOps is about breaking down the barriers that have traditionally separated two typically separate teams. It enables developers to swiftly and independently build, integrate, and validate their code.
This approach encourages collaboration between the development and operations teams throughout the process of the software application life cycle, beginning with the development and testing phases and continuing on through deployment and operations.
How does DevSecOps work?
As said earlier, “DevSecOps,” is a methodology that integrates culture, mindset, a development platform, and automation in order to make security an essential or integrated component.
More often than not, it is considered as the subset of the DevOps methodology. The idea behind the creation of DevOps was to facilitate more productive collaboration between system administrators and software developers.
The goal of merging software engineering and IT operations was to create an IT infrastructure robust enough to run the new program.
Inadequate communication resulting from the quick speed of software development and delivery led to frequent service failures that were costly for businesses and had a bad influence on user experience.
DevOps advocated for rapid software development, unrestricted collaboration, openness to feedback, a focus on transparency, and a willingness to try and fail quickly.
When it comes to IT, it was always considered an afterthought and an extra step in the software development process. In many cases, the security was handled by a separate team at the very end of the development cycle.
DevSecOps changed this by making security in all stages of software development everyone’s job and integrating it more deeply into the CI/CD pipeline.
It guarantees the program’s security from the start of development without slowing down the SDLC. It places great emphasis on employing automation to achieve secure development methods.
Instead of having a dedicated staff look into security issues and fix them at the end of development, developers are tasked with producing bug-free code and including security measures from the start.
How is DevSecOps different from DevOps?
DevSecOps is a subset of DevOps. The agile software development life cycle (SDLC) is used in modern software development to speed up the process of developing and delivering software releases, including upgrades and bug fixes. However, the agile framework is utilized in distinct ways by DevOps and DevSecOps practices.
DevOps places emphasis on the pace of software delivery. Whereas, DevSecOps enhances speed with security by delivering programs that are as secure as feasible in the shortest amount of time possible.
DevSecOps facilitates the rapid creation of a secure codebase. DevSecOps methodology aims at integrating security into each stage of the software development life cycle (SDLC), from build to production.
Continuous and adaptable collaboration between the development, release management (or operations), and security teams are at the heart of the DevSecOps methodology. Every stakeholder in the DevOps value chain is jointly and severally responsible for the system’s security when using the DevSecOps methodology.
DevSecOps may be seen as an evolution of the DevOps concept as it adds a layer of security to the continuous development and operations process. With DevSecOps, security isn’t an afterthought; rather, Application Security teams are brought in early to reinforce the development process from a security and vulnerability mitigation standpoint.
What are the advantages of utilizing DevSecOps tools?
1. Saves Time
The use of automation to improve security is strongly encouraged by DevSecOps. The best thing about incorporating DevSecOps methodologies is that they do not disrupt software development operations. As said earlier, DevSecOps is a subset of DevOps, which is linked with rapid and frequent development cycles.
And the best DevSecOps tools come in handy in such a situation. Earlier, when developers used to create codes, they were inspected for security flaws before they could be merged with other developers’ work. Because of this, it took much longer, which is a leading cause of security breaches.
However, by adding an automatic security check before the merging, developers are able to rapidly identify problems without having to spend hours working on them. DevSecOps tools cut down on the amount of work and assist a team keeps up with the rapid development cycles that DevOps requires.
2. Secure Software Development
Another advantage of using DevSecOps tools is that these technologies make the system more secure. DevSecOps prioritize security. When they are pressed for time or resources, the team may frequently place a higher priority on speed than on security and forego doing some checks that they believe unnecessary. However, with DevSecOps, security is taken care of at each stage of the software development life cycle.
It ensures that each line of code is subjected to all of the checks and scans before it may develop into a problem. Also, it makes using third-party plugins or solutions pretty easier for developers as they don’t waste time testing those plugins. They do it using software composition analysis tools to perform scans of all the plugins.
Other Tools: Top RevOps Software Tools: Reformation for your Business
3. Collective Responsibility
DevSecOps is a cross-team, collaborative methodology that brings together developers and application security specialists early in the software creation process.
Rather than segregated, disjointed operations that inhibit innovation and even lead to split among business divisions, DevSecOps helps teams to get on the same page early, leading to more efficient teamwork.
4. Reduce Security Flaws
One of the main benefits of DevSecOps is it produces a simplified agile development process – an approach that, if done effectively, may dramatically decrease security flaws.
In a nutshell, DevSecOps solutions assist development teams in rapidly developing apps without jeopardizing data security, interfering with ongoing operations, or slowing the process.
Let’s now move to the DevSecOps tools list, which we have compiled for you; take a look…
10 Top DevSecOps Tools
1. GitLab
At number one, we have GitLab, one of the best DevSecOps tools used by developers worldwide. GitLab is a platform for collaborative software development as well as an open-source code repository that is designed for use with large-scale DevSecOps and DevOps initiatives. It offers a location for the online storage of code. Also, it enables continuous integration and continuous deployment, and problem tracking.
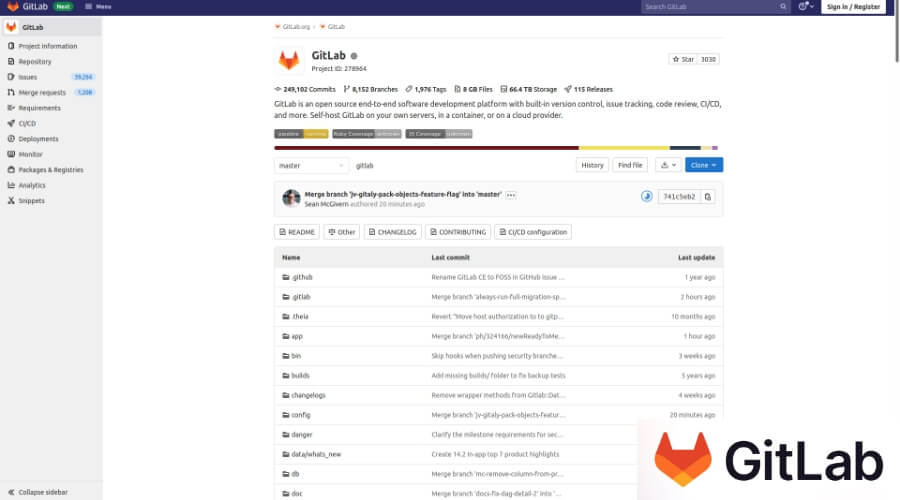
The repository enables the hosting of numerous development versions and chains, and it permits users to inspect previously written code and revert to an earlier version in the event that unforeseen issues arise.
GitLab provides comprehensive DevOps capabilities, covering every stage of the software development life cycle from beginning to conclusion. It comes with Continuous Integration (CI) feature that enables developers to automate the process of building and to test their codes.
The tool incorporates security elements, and the results of scans are provided to developers as part of their continuous integration pipeline or workflow. In addition, a dashboard assists professionals in the security industry in managing vulnerabilities. It also assists in fuzz testing.
Principal Attributes:
- It offers practical planning tools to keep everyone in sync.
- It allows portfolio management and planning via epics, groups (programs), and milestones to organize and measure progress.
- User-friendly that fits the demands of both small teams and large organizations.
- GitLab allows teams to seamlessly organize, schedule, align, and manage project work.
Pricing:
- FREE (for individual use only): Offers only basic features.
- Premium (for team productivity and coordination): $19/month.
- Ultimate (for organization-wide security): $99/month.
2. Acunetix
Acunetix is a web application security-focused DevSecOps tool used to scan and test web apps. It performs a security review of your online applications, looking for flaws such as SQL Injection, Cross-Site Scripting, and others. One of its essential components includes AcuSensor, which is used to inspect source code.
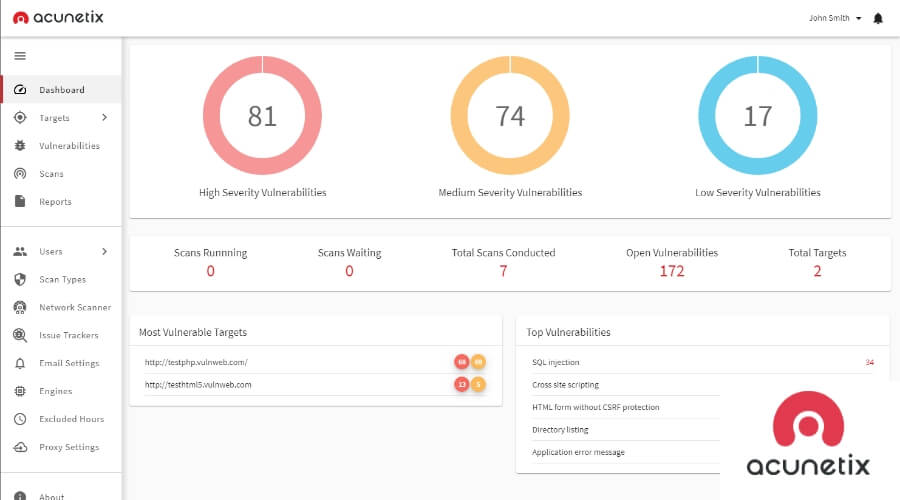
Premium versions of the product provide support for a variety of application programming interfaces (APIs) as well as websites and web applications for delivering content. With onsite facilitating support, AD-based client executives, and Git storehouse support, the Enterprise version even makes the product available for individualized enhancement combination.
Principal Attributions:
- SQL Injections
- Web-Application Security
- Incident Management
- Vulnerability Scanning
Pricing:
- Standard Version: $4,500 (includes all of the main capabilities).
- Premium Version: starts at $7,000 (includes additional support for persistent checking as well as a few other components).
3. Codacy
Codacy is a computerized code audit arrangement that includes a static code examination instrument. This instrument enables programmers to identify potential security flaws in the code while it is being written, which is a significant advantage for software developers.
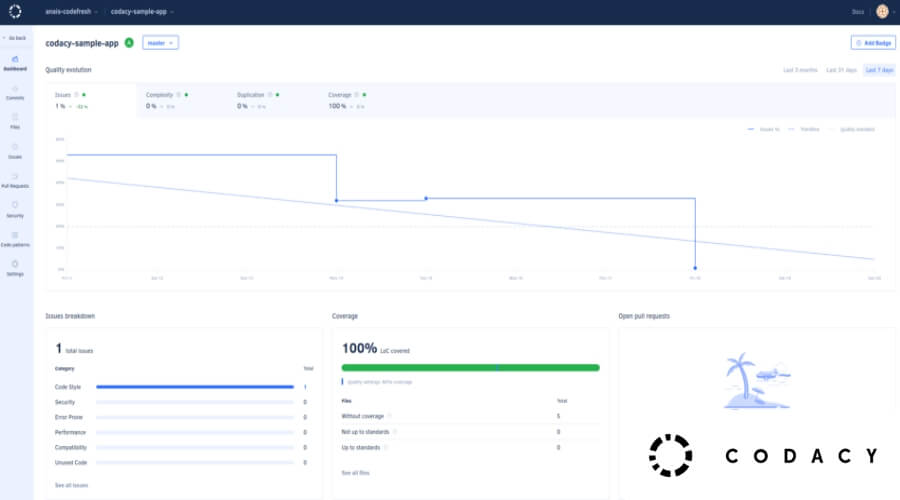
It is a significant DevSecOps tool that substantially reduces long-term security flaws. Also, it helps in other areas of development, such as style rules and duplication issues.
The system offers support for more than 40 languages and is compatible with Git repositories, making it adaptable to varying circumstances. There are a few options available, each of which takes into account pre-programmed live-code surveys that will alert you if a potential security risk is found.
Codacy is a tool for automated code analysis and quality assurance. It enables developers to deploy higher-quality software more quickly. With Codacy, you automatically receive updates to the static analysis, cyclomatic complexity, duplication, and code unit test coverage.
This tool can help you speed up the process of onboarding developers, enforce your code quality standard, save time during code reviews, enforce security best practices, and save time.
Principal Attributes
- Computerized analysis of the code
- Git co-ordinations
- Investigation of the static code
- It offers option for live audit
Pricing:
- Free: for open source
- Pro version: $18 per month.
4. Checkmarx
Checkmarx is one of the most comprehensive AppSec platforms. It comes packed with a wide variety of specialized utilities that may be used to produce and analyze the source code of your application for vulnerabilities in security.
It offers services such as infrastructure as code security testing (KICS), software composition analysis (SCA), static and interactive application security testing (SAST and IAST), and application security and training development (Codebashing). All of these are used to check open-source code.
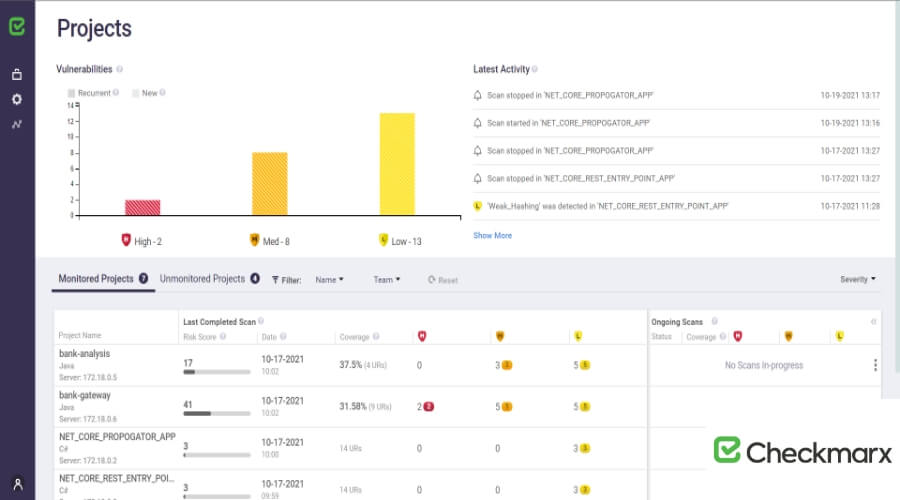
Static Application Security Testing (SAST) is the first technique used by developers of taxi apps. This technique examines your source code while it is being improved and provides insights into any problems that may exist.
These modules could be bundled into the Application Testing Platform, which combines all of the characteristics of a coordination stage for automated CI/CD combination.
Principal Attributes
- Allows for testing for vulnerabilities in the source code
- It is compatible with a wide variety of programming languages and integrates with a number of important CI/CD frameworks.
- SAST scans application source code during software development to identify vulnerabilities and prioritize and swiftly fix security issues.
- Integrate and automate security testing without causing any disruptions to workflows.
Pricing:
- Price per 50 users: $18,000/year
- Price per 100 users: $36,000/year
- Price per 250 users: $90,000/year
5. Prisma Cloud
At number five on our DevSecOps tools list is Prisma Cloud. Prisma Cloud is the most comprehensive Cloud Native Application Protection Platform (CNAPP) available. It provides code-to-cloud security in and across all clouds.
This enterprise-level solution detects vulnerabilities, misconfigurations, and violations of consistency everywhere in a codebase, including within Git archives. Prisma has collaborated with an additional system known as Bridge crew to provide the highest possible level of security inclusion based on open-source foundations.
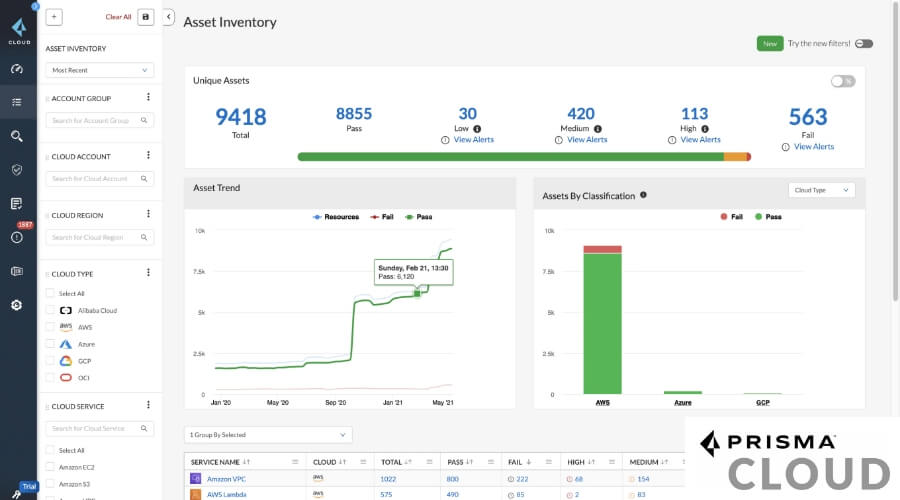
It analyses the current state of your live DevOps environment, offers automated feedback on various security concerns, and can function as a whole git vault vulnerability assessment instrument.
Principal Attributes
- Open-source establishments
- It is the industry’s most comprehensive Cloud Native Application Protection Platform (CNAPP).
- It provides code-to-cloud security in and across all clouds.
- It offers live feedback.
- It makes use of a credits-based authorizing system.
Pricing:
- Business Version: $90
- Enterprise Version: $180.
- In addition, you have the option of requesting a free trial directly from the company.
6. SonarQube
Developed by SonarSource, SonarQube is an open-source platform designed for continuous code quality monitoring. It offers constant inspection of code quality, performs automatic reviews with static analysis of code, and detects bugs and code smells in 29 different programming languages.
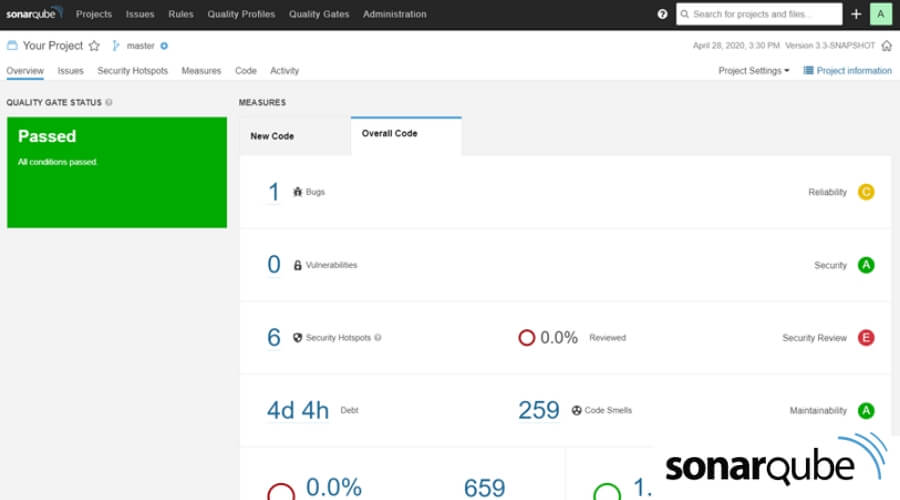
It does a comprehensive check of your program’s source code to identify potential vulnerabilities and safety flaws. The premium version of SonarQube offers Taint Analysis. It examines client data and scrubs it clean of any harmful compounds before sending it on to fundamental frameworks.
It is simple to configure the tool for use with a JavaScript project, and it is compatible with other technologies that facilitate continuous integration and continuous delivery.
Principal Attributes
- Investigation of the static code
- Controlled dissemination of information
- Free and open-source software (with premium updates)
- Consistency in the pursuit of and revelation regarding CI/CD combo
- Supports 29 languages
Pricing:
- Developer Version: Starts from $150
- Enterprise Version: Starts from $20,000
- Data Center Version: Starts from $130,000
7. ThreatModeler
ThreatModeler is one of the best DevSecOps tools available for conducting security audits. It automates the threat modeling and response processes.
The ThreatModeler solution, in conjunction with CloudModeler and IaS-Assist, enables DevOps to safeguard their IT infrastructure and applications. Users can design, construct, and manage security from development to deployment with the help of the ThreatModeler platform. This software quickly visualizes their attack surfaces, helping to reduce security vulnerabilities and threat drift in software development life cycle (SDLC) processes.
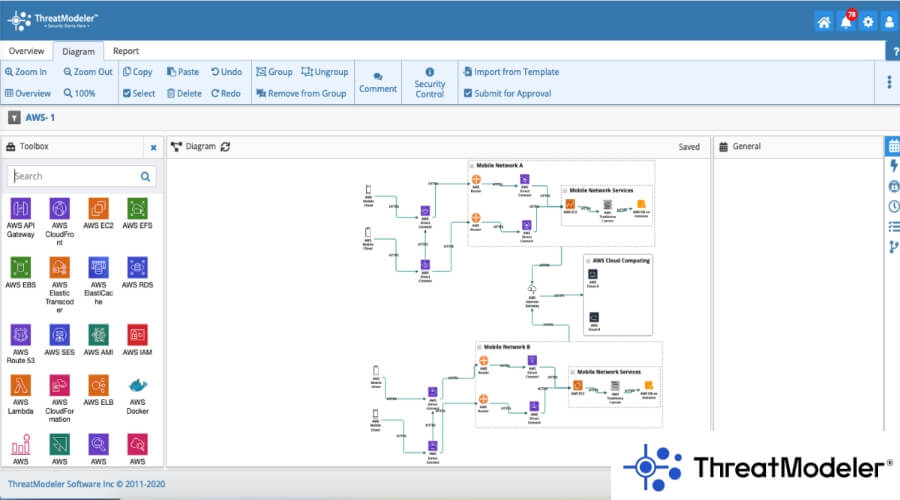
The latest addition to ThreatModeler’s software suite, IaC-AssistTM, uses infrastructure as code (IaC) to provide ongoing visibility into previously unknown security vulnerabilities in application architecture. This robust extension for AWS allows developers to code with confidence without leaving their IDE.
Principal Attributes:
- Enterprise-grade cloud migration and deployment with increased speed and safety.
- Effective across the board in DevOps services and other clouds, mobile, IoT, and web environments.
- A more rapid and safe transition to the cloud for businesses.
- Allows for continuous, real-time visibility into previously hidden design defects by means of infrastructure as code (IaC).
- Ability to personalize risk libraries on a project-by-project basis
- Compatible with well-known software programs such as JIRA and Jenkins.
Pricing:
- One Year License: $4,000
- You are required to contact the ThreatModeler firm to obtain a personalized demonstration and price quote for the ThreatModeler DevOps Edition, which features complete CI/CD integration.
8. CyberRes Fortify
CyberRes Fortify is an enterprise-level application security platform that employs AI-driven scans to quickly discover and cure security issues. The platform provides protection against a wide variety of threats.
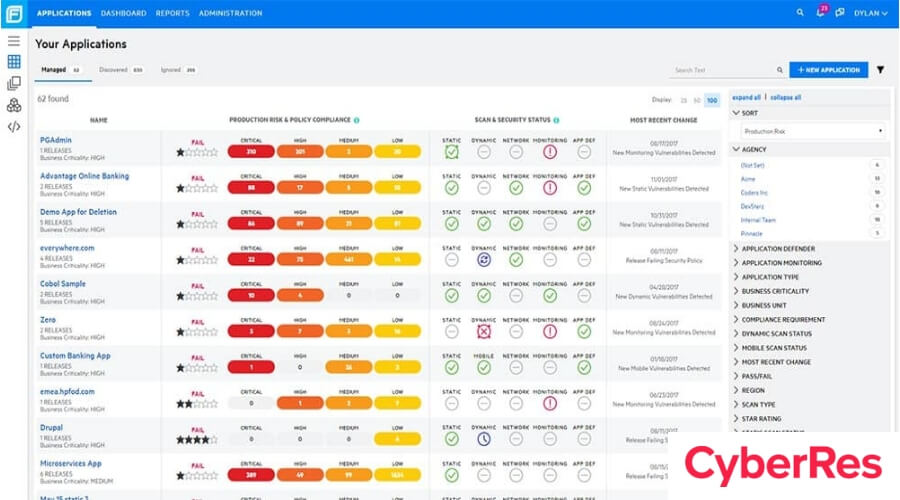
In addition to this, the solution is capable of automating testing in a live CI/CD integrating environment, and it comes with a set of plugins for integrated development environments (IDEs), integration with Jenkins, and other capabilities that enable modular deployments wherever the product is needed.
On-location hosting is the primary selling point of this product. This means that it can be hosted on the customer’s premises for increased levels of safety. This solution makes use of a number of different analyzing engines to investigate the code and identify any possible errors. This configuration can be fed specific rules to provide context for the scan, and it can be carried out using a command line interface (CLI) or an integrated development environment (IDE).
Principal Attributes
- Security for Apps
- Examination of risks and exposures
- Software composition analysis
- The study of static code
- Plugins for granular control
- It offers an uncomplicated user interface
- Provides support for integrations with CI and CD
- It offers onsite hosting
Pricing:
- Free Trial: Available for 15 days.
- If you want a personalized estimate of the cost of the whole product as well as the individual plugins, you will need to get in touch with the company directly.
9. IriusRisk
IriusRisk is yet another wonderful DevSecOps tool. This automated threat modeling solution can assist you in locating security vulnerabilities in your DevSecOps projects. Also, it can assist you in developing mitigation strategies for those vulnerabilities.
Using IriusRisk, developers can plan security work prior to coding and deployment. IriusRisk utilizes pre-defined components and a built-in threat and countermeasure library to enable teams to construct these models without the assistance of security professionals.
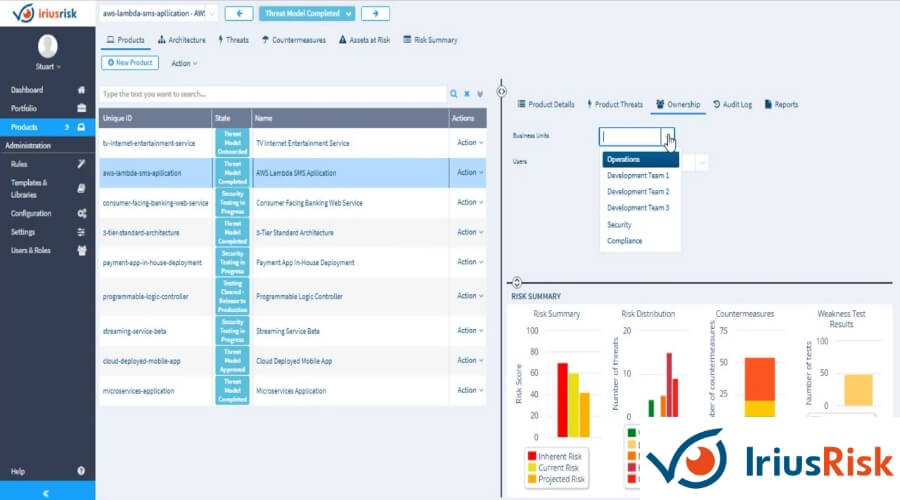
Countermeasures can be deployed straight to ALM systems such as Jira, TFS, and Rally, putting them at the forefront of developers’ workflows. IriusRisk is compliant with the industry’s most prominent standards, including PCI DSS, EU GDPR, OWASP, and NIST 800-53. It allows for comprehensive API and native integration with the majority of DevSecOps pipeline products.
The free edition of IriusRisk, which integrates with draw.io to eliminate costs while preserving significant threat modeling tools, is where this product truly shines. There is a premium edition available for purchase, as well as an Enterprise version, which extends the capabilities of the software even further. So, if you work on a lot of large-scale projects, it could be worthwhile to opt for the Enterprise version to have access to improved importing and exporting features as well as API access for an unlimited number of threat models.
Principal Attributes
- Integrated Development Environment (IDE) for the generation of automated tests.
- It offers numerous opportunities for export and import
- It offers tools for modeling that are simple to use
- It lets you create a threat model in a few minutes
- Identify product vulnerabilities and countermeasures.
- Avoid deployment delays and accelerate time-to-production.
- Access to the API is provided for major projects under the Enterprise edition.
Pricing:
- FREE: Offers only basic features.
- AWS Version: $110 per month
- Enterprise Edition: You will need to get in touch with the sales team directly in order to receive a customized quote on the price of the Enterprise edition.
10. StackStorm
Last but not least, StackStorm is one of the best DevSecOps tools that developers use. It is an open-source event-driven platform for runbook automation. It has been compared to SaltStack and Ansible and supports the Infrastructure as Code approach to DevOps automation. Its primary focus is on doing things or executing workflows depending on events, and it offers support for the methodology.
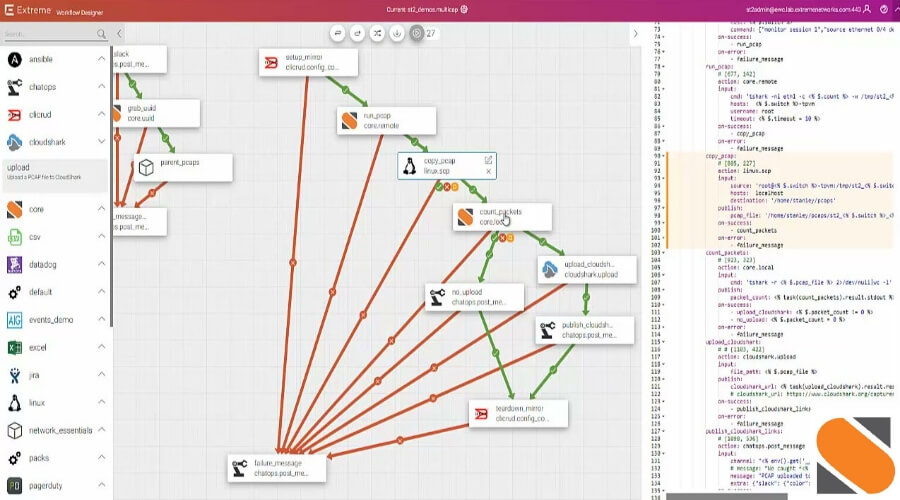
StackStorm, co-created by developers Evan Powell and Dmitri Zimine, is an automation platform that is similar to IFTTT and Zapier and allows users to link numerous services into unified “applets” or “workflows” that kick off in response to predetermined events.
This automation solution for DevOps is even used by reputable companies, including NASA and Netflix. They have constructed the solution using an If-This-Then-That (IFTTT) architecture; sensors detect a trigger, which is then mapped to actions by a set of rules that they have developed.
In addition, StackStorm provides an audit trail that tracks each action, trigger, and the results of how the activities were carried out. They have a wide variety of integrations, which can link this to various analytics tools.
The StackStorm packs, which are essentially collections of triggers, actions, and workflows tailored to specific applications, are an intriguing and useful component of the StackStorm platform. You have the option of either creating your own packs or getting them from the StackStorm exchange.
Principal Attributes
- It is an open-source, event-driven platform.
- It allows you to set conditional logic for anything you want.
- Python plugins for inbound or outbound integration.
- It offers an easy-to-use user interface.
- StackStorm Enterprise provides 24×7 support.
Pricing:
- StackStorm Community: FREE
- StackStorm Enterprise: $500
Wrapping it up…
So, there you have it: the list of 10 top DevSecOps tools. All of the tools mentioned above are the best DevOps projects. You can make use of any of these tools.
These DevSecOps tools help companies incorporate security best practices and standards into the DevOps workflow, particularly at the outset of the software development lifecycle.
Using the best automation tools in the areas of development and information security operations can help businesses increase productivity, reduce errors, and ensure that security measures are implemented consistently.
Also, these tools can help you incorporate compliance into the delivery process. Not only will you be able to find security flaws in the beginning of the software development process, but also you would be able to keep everything in order and check.